Production environments can be tricky
Having custom authentication providers because of less than secure legacy systems can be just one of the problems you face when securing an API.
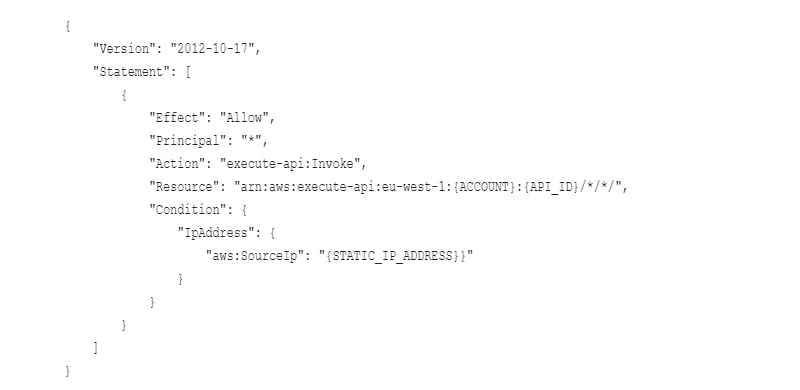
We also have a requirement to secure the api so that only the clients static IP address be allowed to access this specific API.
The simplest route to achieve IP Filtering is to setup a resource policy on the API itself, the snippet below will allow access from a specific Static IP address to execute your API
When configuring your Resource Policy, there is a banner at the top:
Configure access control to this private API using a Resource Policy. Access can be controlled by IAM condition elements, including conditions on AWS account, Source VPC, VPC Endpoints (Private API), and/or IP range. If the Principal in the policy is set to *, other authorization types can be used alongside the resource policy. If the Principal is set to AWS, then authorization will fail for all resources not secured with AWS_IAM auth, including unsecured resources. Learn more.
Which is fairly misleading as it states “private API“ this is not true and I successfully used the snippet above on a Regional Endpoint.
Please note that changing an Edge Optimized endpoint to a private endpoint will not allow you to change it back to an Edge Optimized endpoint there after.
I tested it using a mock Method and the Resource Policy above

Select "Select Create Method"
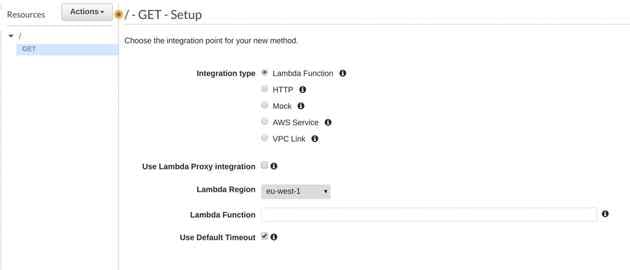
Set Integration Type to Mock
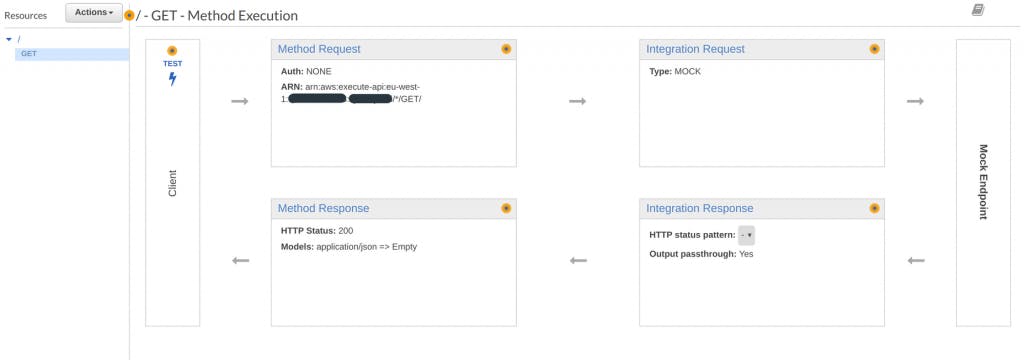
Extract your method ARN to be placed in the Resource Policy, you can also use wildcards such as * for multiple characters and ? for single characters
The next step is to test your API on 2 different external IP addresses, I used my own machine wich was on the current network and my android device which was on the cellular network
Go To Stages → Your Stage and then you will see an Invoke URL at the top, if you have a GET method you can use this in your browser to test your response
A request that comes from an Invalid IP address will return a 403 and get a message that looks like this:
{
"Message": "User: anonymous is not authorized to perform: execute-api:
Invoke on resource:
arn:aws:execute-api:eu-west-1:************:**********/#STAGE#/GET/health"
}And that concludes how to setup IP filtering on API Gateway, hope this helps someone out there.